Inserting the keys into hash table
Open addressing is the hashing technique in which for inserting an element in the table firstly we search for the elements if it is already contained in it, the search returns either the element or the free space in the array to fill that element.
In uniform hashing technique sequence of elements to be search
can be any of the m! permutation in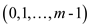 that is this
technique gives the method of searching which search in the full
list for the single element in the generalized way.
that is this
technique gives the method of searching which search in the full
list for the single element in the generalized way.
When the first key inserted, it has m choices out of
m, the second key has 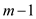 choices out
of m so on, key n has
choices out
of m so on, key n has 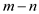 choices out
of m. The insertion of these keys is independent of each
other,
choices out
of m. The insertion of these keys is independent of each
other,
Thus probability:
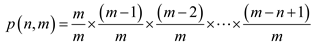
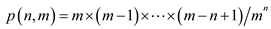 ……(1)
……(1)
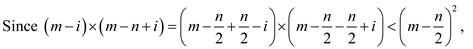
Hence from equation (1) the probability is as:
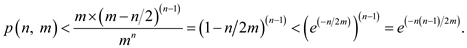
By theorem for the n keys to be inserted in a table where
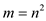 then the probability of occurring a match in the table is less
than
then the probability of occurring a match in the table is less
than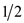 , it is very
efficient to find the hash function for which there is no
collisions in a static set K containing n keys.
, it is very
efficient to find the hash function for which there is no
collisions in a static set K containing n keys.
When the number of key values n exceeds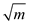 , that is a
hash table of size
, that is a
hash table of size 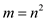 that is
that is
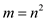 is
excessive. Hence in this case we use the hashing technique at the
two levels, in the first level or at the outer level the hash
function
is
excessive. Hence in this case we use the hashing technique at the
two levels, in the first level or at the outer level the hash
function 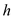 to hash the
keys into
to hash the
keys into 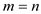 slots.
Then, if
slots.
Then, if 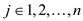 the
the keys
hash to slot j. we use a secondary hash table
keys
hash to slot j. we use a secondary hash table  of size
of size
 it
gives a set having invariant or constant time without any
collisions in the table.
it
gives a set having invariant or constant time without any
collisions in the table.
Hence, in a hash table of capacity m for inserting
n keys by open addressing and uniform hashing techniques
then the probability of collisions to occur is 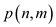 where
where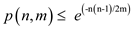 .
.