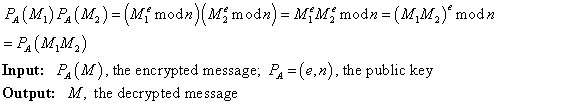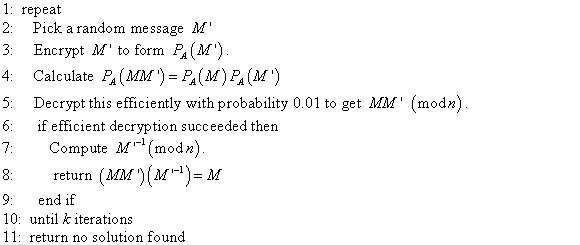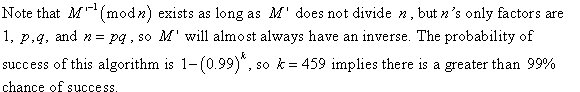Consider the following RSA key set to determine the value of d that is used as the secret key.
The provided value of p, q n and e are as follows:
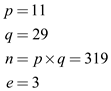
Calculate the value of 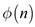 using the
formula
using the
formula 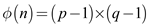 .
.
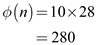
Compute the value of d using Extended-Euclid’s algorithm
such that 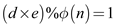
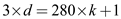
where k is the least positive integer.
For 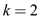

Therefore the value of the secret key is 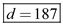 .
.
Calculate the cipher text of the message 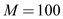 .
.
The formula to calculate the cipher text is  .
.
where c is the cipher text.

Therefore, the encryption message of the message
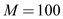 is 254 .
is 254 .
If Alice’s public exponent 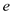 is chosen as
3, then it is insecure.
is chosen as
3, then it is insecure.
Suppose that when a same message that Alice want to send to several different people.
• Now, if Alice does the obvious thing as encrypting the message which have to send using each of their public keys and send it.
• Then eavesdropper Eve will collect every encrypted message.
Now, Eve will check if the number of messages is equal to or
greater than the encrypted exponent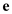 , then in
this condition Eve may recover the message.
, then in
this condition Eve may recover the message.
Consider the following example:
Suppose Alice’s want to send the same message 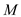 in the
encrypted form to a number of different several people
in the
encrypted form to a number of different several people , where
every using the same exponent
, where
every using the same exponent 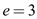 and
different modulo
and
different modulo .
.
Suppose the eavesdropper Eve intercepts  and
and
 where,
where,
 .
.
Then,
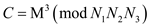
However,
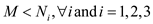
Then user consists the following:

Thus, 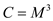 holds over
the integer and then Eves can easily obtain the cube root of
holds over
the integer and then Eves can easily obtain the cube root of
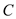 to
compute
to
compute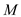 .
.
Hence, if the exponent 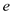 is chosen to
3 or
is chosen to
3 or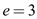 ; then only
three different encryptions are sufficient to recover the original
message.
; then only
three different encryptions are sufficient to recover the original
message.
Therefore, from the above explanation it is clear that, “if
the exponent 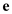 is
chosen to 3, then the adversary can factor Alice’s modulus
n in time polynomial in the number of bits in
n”
is
chosen to 3, then the adversary can factor Alice’s modulus
n in time polynomial in the number of bits in
n”